If you are planning to migrate from the existing SAP Business Suite to SAP S/4HANA, one of the most important factors is the change in security. The modifications in security occur due to changes in technological and architectural patterns in SAP S/4HANA. However, it is vital to understand the critical areas that need to be considered when boosting the security of an S/4HANA implementation. Besides, it is important to know about the various SAP resources that play a role in implementing a secured setup and running SAP S/4HANA.
With SAP announcing that it will stop supporting its HANA module, most business organizations have either moved to S/4HANA or are planning for a transition. SAP security administrators will have to mainly address five important factors when migrating a business app to an advanced ERP system. They are-
- Roles and Authorizations
- SAP HANA Security
- Infrastructure Security
- Cloud Integration
- Management and Authorization
It is also essential to identify the key challenges that may arise while strengthening the security of S/4HANA implementation. So, it will be useful if you first get familiar with security activities related to S/4HANA migration. You will also get to know what technology and architectural changes will occur in security when you move to S/4HANA.
Changes in Technological Security Landscape of SAP S/4HANA
SAP NetWeaver AS ABAP (Advanced Business Application Programming) is the core system for both SAP HANA and S/4HANA. It is a conventional SAP Business Suite operating on the SAP HANA database. It contains internal upgrades, standard security controls, and switches needed for other SAP NetWeaver AS ABAP systems.
You also need to note that SAP HANA doesn’t only act as a database but also as an application server. The ERP Business Suite allows some of the S/4HANA application processes to natively operate from it. It means you can run your S/4Hana applications natively from SAP HANA extended application services. SAP security administrators also need to take note of native SAP HANA applications that evade ABAP stacks and security controls. SAP S/4HANA also simplifies the business processes with the help of SAP Fiori apps and cockpits. For instance, the vendors can directly enter the number of receipts or bills into your system to check the information. However, you have to take into consideration the underlying network security infrastructure as accessing the ERP functions can influence it.
Business enterprises are also moving on to the cloud and S/4HANA offers various options to integrate cloud-based systems into a hybrid landscape. It means that the crucial data is present in some other place apart from the on-premise location. The security team has to keep a close eye on implementing security along with external applications and systems. Their work also includes coordinating access with all different applications and instances so that managing authentication becomes more seamless, efficient, and centralized.
Securing the SAP S/4HANA Implementation
Once you have migrated SAP HANA ERP Suite to SAP S/4HANA, you need to quickly focus your attention on enhancing the security of the S/4HANA landscape.
Upgrading Roles and Authorizations
So, the first step of securing the SAP S/4HANA landscape is going for an update. It means you need to upgrade your roles and authorizations. For instance, you will have to do new checks for authorization objects. SAP has introduced this facility to protect business data and functions against unauthorized checks. Apart from that, you also have to view new old transactions, which requires substantial effort. If you have a thorough knowledge of security transactions on Maintain Check Indicators (SU24) and Upgrade Tool for Profile Generator (SU25), updating roles and authorizations will rather become smoother.
SAP S/4HANA also includes SAP Fiori apps that are usually web services. Authorized users are allowed to use the apps. Configuring authorization isn’t a tough task. But the main challenge is to create roles based on design changes in S/4HANA. It can prove more difficult for users who are unfamiliar with SAP Fiori apps and its publishing process using SAP Gateway. Role Building Administration PFCG, which helps in managing roles and authorization data, combines new techniques to integrate app catalogs as well as synchronize with SAP Gateway. Security will have to comprehensively understand the entire working procedure of role building in transaction PFCG based on the SAP S/4HANA landscape.
SAP HANA Security
The data security administration team relying on cloud deployment solutions (on-premise or in the cloud) also has to gain knowledge on new security systems and authorizations related to the SAP HANA database. They need to run it properly and protect it from any unauthorized access. SAP HANA version 1.0 required administrators to directly access database SQL. It is because SAP HANA studio was connected with the database SQL port presenting security challenges.
But today the scenario has changed and SAP HANA development and administration are generally carried out through web interface. Soo, the security team has to just access the application server’s web service port. However, if you are not able to access the web service port or a key development functionality is missing, you can gain access via SQL port. But you have to choose an established workplace. Examples include Windows Terminal Server (WTS) workstations.
The administrators are required to take note of new authorizations designed by SAP HANA for extended application services and advanced models. The extended application service and advanced model was unveiled with the release of SAP HANA version 2.0. So, you need to understand that creating roles and authorizations for version 2.0 is different from the conventional database and SAP application server security system. If the business enterprise wants to develop a new native application, an adept SAP Consultant Company with adequate knowledge on SAP HANA security design will do the job.
SAP has provided new features in extended application service and an advanced model. However, they are only needed for advanced processes. Standard S/4HANA apps do not require an SAP HANA custom extended application service or advanced model.
Robust Security Infrastructure
As more businesses are implementing a digital transformation, it is opening the gate to opportunities where they can customize and innovate their services to surge customer experience. With SAP joining hands with blockchain technology, the transaction process has become more secure, simplified and streamlined. Instead of employing a traditional approach, it is processing payments in real-time.
Earlier, it was difficult for external users to get access to a few parts of business applications due to a closed-shop the SAP world. Moreover, the other issue was the SAP GUI that was connected to established network ports. Users saw it as an SAP Enterprise Portal.
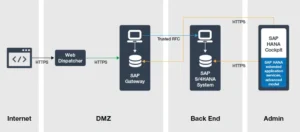
However, SAP S/4HANA has got the support of SAP Fiori technology, which has simplified the process of app publishing to other user groups, mobiles or desktops. Apart from that, S/4HANA also protects access to business-critical-system components. It ensures that users have access to the right set of apps with enforced security controls such as two-factor authentication. Make sure that the SAP Gateway is a Demilitarized Zone (DMZ) and S/4HANA gains internal high security.
The administrative team has to necessarily secure the data transmissions in the architecture using a standard process like Transport Layer Security (TLS) protocol. The team has to strengthen the security of scenarios in which HTTPS and Remote Function Call (RFC) connections cross network zones using reverse invoke.
Team coordination is very essential. The different teams that work on SAP S/4HANA security include Operations, Portal, Security Firewall, and Networking. They must incorporate every step or requirement to boost the security of S/4HANA.
Implementing the Cloud Application
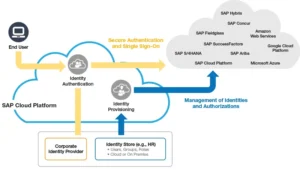
SAP has also found a viable solution where the administrator does not have to permit external user groups to access on-premise applications. Rather, the users can easily interact on cloud solutions, which is more secure as well. A wide range of activities are being carried out on a cloud and SAP S/4HANA is not behind in offering a simplified platform to conduct data exchanges in real-time environments. For instance, the SAP Cloud Platform can easily exchange data Cloud Connector and connect SAP Cloud Applications with on-premise systems.
If the security team is providing support to a hybrid business process, it has to implement SAP S/4HANA on-premise as well as in-cloud. They should also be familiar with the process of setting up and running Cloud Connector securely and simply. They should know how to grant permission to cloud applications using the SAP Cloud Platform Identity Authentication and SAP Cloud Platform Identity Provisioning services. Make a comparison between the setup of Cloud Connector with SAProuter and Web Dispatcher installations.
Management of User Access and Authentication
Digital business environments often face the challenges of establishing the right coordination with different types of access, specifically if access takes place across hybrid landscapes. You will have to set up users in SAP S/4HANA as well as natively. Users should have access to SAP Gateway, which offers application catalogs and entire connected cloud apps. It also streamlines transfers between individual systems. It will prevent password promotions again and again.
When managing the user access and authentication for implementing the modern S/4HANA security system you should know federated single sign-on and Security Assertion Markup Language (SAML) version 2.0. They have a task in hand to create an efficient Identity Management Solution to simplify the work of tracking individual accounts.
The solution will help to serve users both on cloud and on-premise systems. You also have to develop a Central User Administration System to maintain both SAP S/4HANA and SAP Gateway in one place. However, you can keep the cloud users separately. It is important to choose the right set of technology when you are migrating from SAP Business Suite SAP S/4HANA.
Additional Support Offered by SAP
SAP also offers some additional support that helps the security team to easily implement SAP S/4HANA security. Let’s have a brief discussion.
Information Available in the form of Whitepapers
To help SAP consulting companies in smoothly securing the S/4HANA transition, SAP has published a series of whitepapers, where every information about security is mentioned in comprehensive detail. The teams can go through these whitepapers to understand the process and implement the same.
SAP Solutions Manager
SAP Solutions Manager offers a System Recommendations application focusing on the important security elements that are not present in the system and Configuration Validation Application. It checks to see whether or not the system has been configured according to security norms.
Security Guidelines and Training
SAP also offers security guidelines and training courses, which help the professional to gain practical and theoretical knowledge on how to fortify the security of SAP S/4HANA.
Identification of Risks and Management Access
If you want to identify the risk factors and security concerns, SAP provides a complete SAP Enterprise Threat Detection for getting access to higher security standards and integration. The facility is offered in the Security Information and Event Management (SIEM) and Security Operations Center (SOC). SAP also provides a single sign-on scenario using Cloud Platform Identity Provisioning and Cloud Platform Identity Authentication. Customers can manage their user access to cloud applications and integrate their identity providers into the architecture. Customers can migrate from cloud applications to on-premise applications and vice-versa without facing any difficulty. Moreover, Cloud Connector helps in offering vital business data whenever required.
SAP Digital Business Services has been specifically designed for those who are stringently particular about security and require external support. The SAP solution focuses on security design and implementation with the help of specific phases. Also, SAP has also introduced the SAP Max Attention, also referred to as New Max Attention with a focus topic to further strengthen security and compliance.
Security For Running Core of SAP S/4HANA
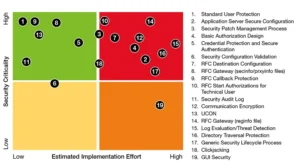
We have discussed the important factors that need to be focused while securely running the SAP HANA landscape. However, we also have to equally pay attention to the core of running SAP S/4HANA. This means emphasizing the SAP NetWeaver AS ABAP system. The Security Administration Team needs to work on the following elements for securing the core.
- Credential Protection
- Standard User Protection
- Secure Custom Code
- Protecting Data Transmission
- Security of SAP Code
- Security while Configuration
- Logging
- Interface Security
You need to note that all the tasks mentioned above are quite important but you cannot start all these activities at the same time. SAP suggests its customers do not conduct more than three tasks in parallel as it can lead to overloading of SAP Basis and Security teams. It is advisable to access the protective measures and then prioritize the activities according to their importance and remediate them. Now, develop the project plan that focuses on emphasizing security based on the run time and ability to gain more users.
Conclusion
Security plays an important and comprehensive role when you are planning to migrate an existing SAP Business Suite to SAP S/4HANA. It allows applications to leverage the full advantage of SAP’s advanced ERP solution. Take into consideration all the crucial factors such as following the new security measures for SAP S/4 HAN, cloud integration scenarios, SAP HANA 2.0 roles and authorizations management, and others. If you are looking to enhance the security of your SAP S/4HANA implementation, it’s time to get in touch with expert SAP consultants, who will help you out in every possible way.